Private Synology Docker Registry

In this article I am going to walk you through how to setup a private Docker registry on your Synology NAS. While Dockerhub offers private repos, you can only have 1 for free.
Setting up the Docker Registry Image
First and foremost, we need to set up our Docker registry image. We will be doing this first configuration setup via the terminal.
Head over to your terminal and SSH into your synology - you will want to do this as root via sudo -i
ssh username@my.synology.ip
>> <logged_in>
sudo -i
Most individuals who are running Docker have a specific docker folder in one of their volumes where they store all their images. Navigate to that folder and we will create another folder called registery
cd /volume1/docker
mkdir registry
We must add to two more folders to the registry directory. auth and data
mkdir auth
mkdir data
The auth directory is where we will be storing a username/password to ensure that our Docker registry is not accessible by anyone who does not have those credentials. To do this, we will be utilizing the Docker cli. Navigate to the auth directory and run the following command:
Note: replace <username> and <password> with a username and password of your choice
cd auth
docker run --rm --entrypoint htpasswd httpd:2 -Bbn <username> <password> > htpasswd
If all runs fine, you should see a new file added in the auth directory: htpasswd

Adding Registry via docker-compose
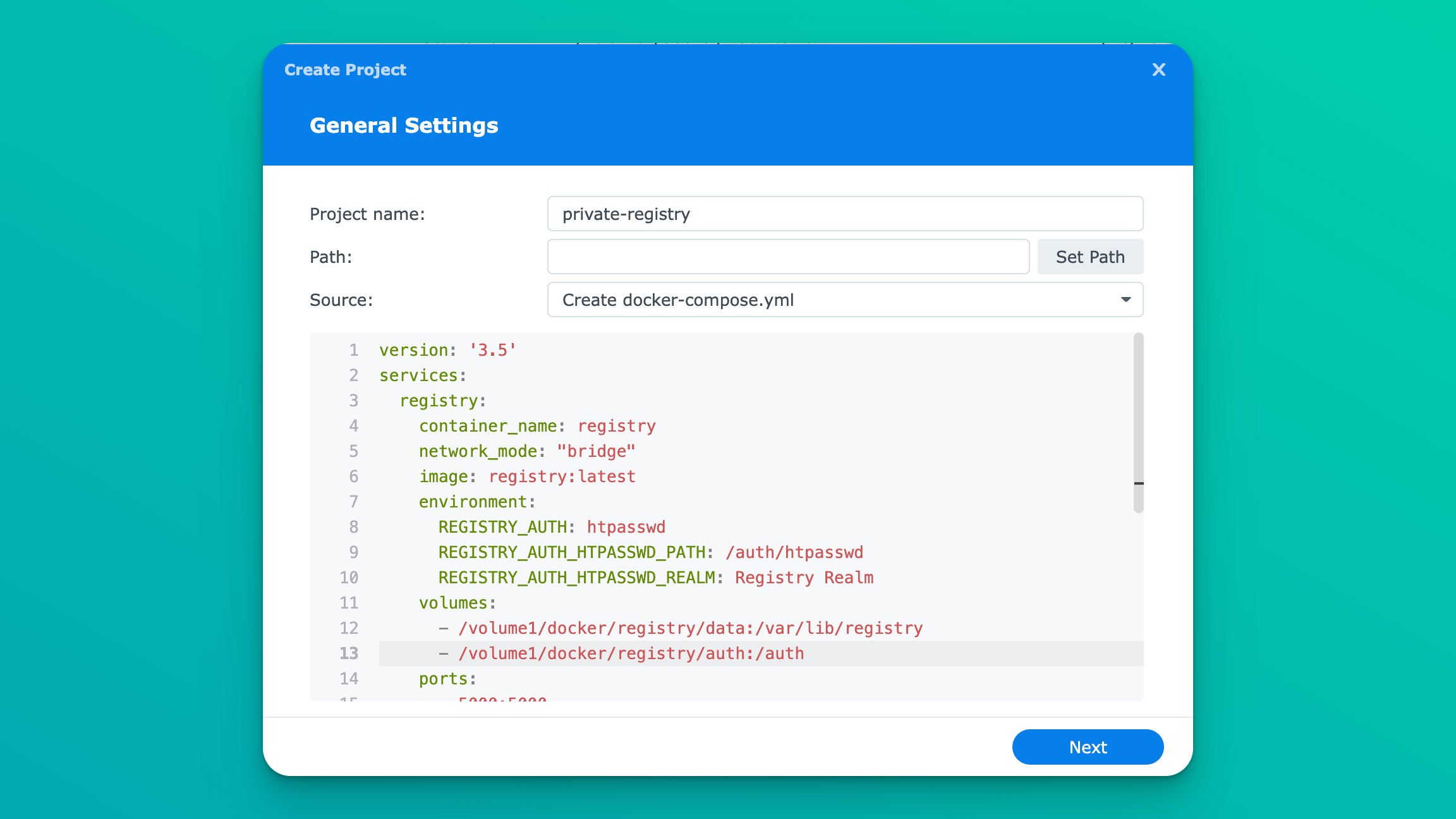
Now we will create a docker-compose to setup the registry. Assuming you are on DSM 7, you can head over to Container Manager, click project, and then create. You will use the following docker-compose:
version: '3.5'
services:
registry:
container_name: registry
network_mode: "bridge"
image: registry:latest
environment:
REGISTRY_AUTH: htpasswd
REGISTRY_AUTH_HTPASSWD_PATH: /auth/htpasswd
REGISTRY_AUTH_HTPASSWD_REALM: Registry Realm
volumes:
- /volume1/docker/registry/data:/var/lib/registry
- /volume1/docker/registry/auth:/auth
ports:
- 6739:5000
restart: unless-stopped
Keep in mind the volume mapping. We set up data and auth in /volume1/docker/registry, however, if you setup your docker information in a different directory, that will need to be reflected here. Additionally, depending on the port you want to expose this on, you would want to change 6739
External access
Now, we would want to expose this so that we can access this registry remotely. You can follow my other article on how to accomplish this via Cloudflare tunnels.
What's next?
Next, we will write an article about how we can use this and GitHub actions to create a simple CI/CD pipeline on your own infrastructure!